Ready IIoT Solutions- Device, Network, Cloud
WoMaster Cloud Solution is a high-level, multi-platform, and flexible application development environment for WoMaster IIoT Gateways such as WR Series and SCB Series. The cloud connects and interfaces with field devices thanks to its ready-to-use Modbus field protocol that connected to the IoT Sensor device. It enables Modbus connectivity for data acquisition and processing, MQTT support for lightweight data transmission, and device management. The field data can be published and delivered directly to leading IoT Cloud Services, ThingsMaster IoT Private Cloud that equipped with Responsive Web Design, where all of the data is stored and accessed for monitoring, visualizing, and controlling purposes. The field data includes Video Surveillance streaming; data from the sensor, device management, and RTSP streaming. It uses the latest TLS encryption and X.509 authentication to protect the data transmission also N-to-N VPN for secured Multi-sites management. The IoT Cloud Service also includes the ThingsMaster OTA, over-the-air device management; it is an interactive monitoring dashboard and map that shows the device status, signal strength, and location. Fault alerts on critical events to prevent downtime can be added by using the flow-based programming tool, Node-RED. Multi-Tenant for Project-based IoT deployment is supported.
WoMaster Cloud Solution helps to accelerate the development of industrial IoT applications and create a smarter field site; it provides smart data acquisition, development, and easy management.
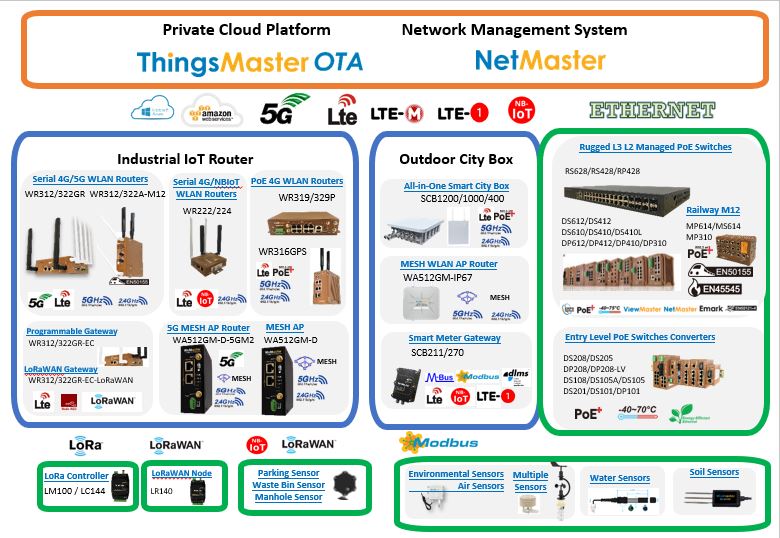
Advanced Cyber Security Design
From the viewpoint of cybersecurity experts, the major cybersecurity threats that can affect internal networks include unauthorized access, unsecured data transmission, unencrypted key data, incomplete event logs, and operational errors. By IEC62443-4-2, the security levels define the cybersecurity functions embedded in WoMaster products. The higher the security level, the more increased product robustness and resistance to cyber threats.

WoMaster provides SW & HW(ASIC) integrated protection mechanism, which applies the latest Application-Specific Integrated Circuit (ASIC) secure technology (L2-L7 packet classification), multi-level authentication, secure data transmission, encrypted key data, complete event logs/traps, operational errors prevention, and event logs, and operational errors exceeds IEC62443-4-2 Level 2 requirements to build the most secure systems for industrial applications.
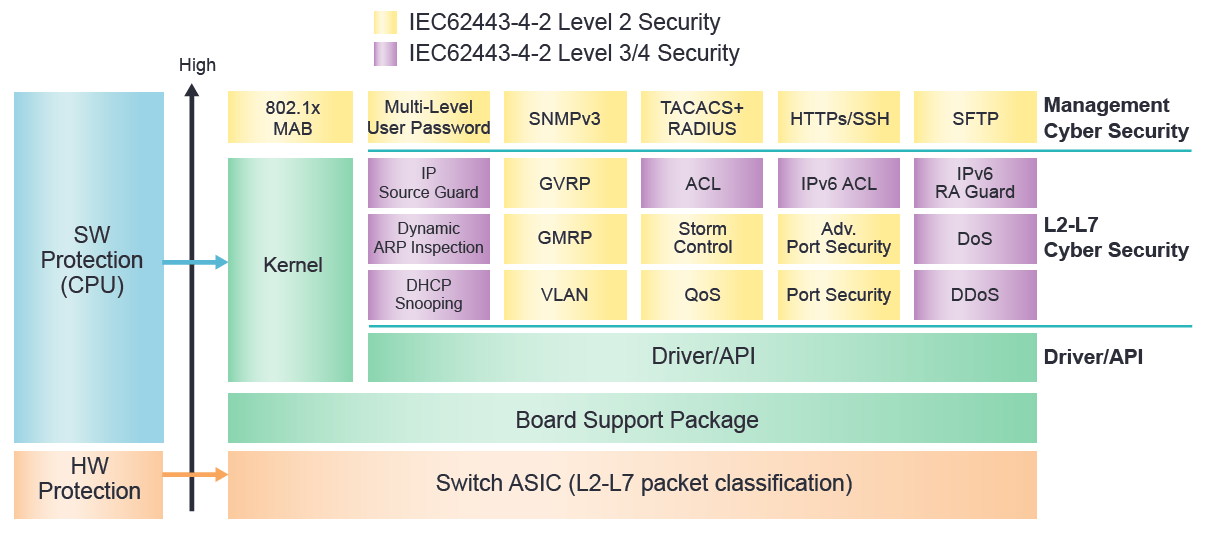
IEEE802.1 x MAB (MAC Authentication Bypass)
MAB enables port-based access control by bypassing the MAC address authentication process to TACACS+/Radius Server. Prior to MAB, the endpoint's (ex. PLC) identity is unknown and all traffic is blocked. The switch examines a single packet to learn and authenticate the source MAC address. After MAB succeeds, the endpoint's identity is known and all traffic from that endpoint is allowed. The switch performs source MAC address filtering to help ensure that only the MAB-authenticated endpoint is allowed to send traffic.
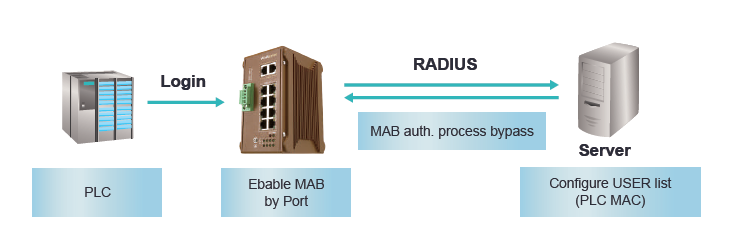
 In addition to MAB, the authentication can also be done by the pre-configured static or auto-learn MAC address table in the switch.
In addition to MAB, the authentication can also be done by the pre-configured static or auto-learn MAC address table in the switch.
.MAC address Auto Learning enables the switch to be programmed to learn (and to authorize) a preconfigured number of the first source MAC addresses encountered on a secure port. This enables the capture of the appropriate secure addresses when first configuring MAC address-based authorization on a port. Those MAC addresses are automatically inserted into the Static MAC Address Table and remain there until explicitly removed by the user.
.The port security is further enhanced by the Sticky MAC setting. If Sticky MAC address is activated, the MACs/Devices authorized on the port 'sticks’ to the port and the switch will not allow them to move to a different port.
.Port Shutdown Time allows users to specify for the time period to auto-shutdown the port if a security violation event occurs.

.The port security is further enhanced by the Sticky MAC setting. If Sticky MAC address is activated, the MACs/Devices authorized on the port 'sticks’ to the port and the switch will not allow them to move to a different port.
.Port Shutdown Time allows users to specify for the time period to auto-shutdown the port if a security violation event occurs.

DHCP Snooping
DHCP snooping acts like a firewall between untrusted hosts and trusted DHCP servers. It performs the following activities:
.Validates DHCP messages received from untrusted sources and filters out invalid messages.
.Rate-limits DHCP traffic from trusted and untrusted sources.
.Builds and maintains the DHCP snooping binding database, which contains information about untrusted hosts with leased IP addresses.
.Utilizes the DHCP snooping binding database to validate subsequent requests from untrusted hosts. DHCP snooping is enabled on a per-VLAN basis. By default, the feature is inactive on all VLANs.You can enable the feature on a single VLAN or a range of VLANs.
Dynamic ARP Inspection (DAI)

DAI validates the ARP packets in a network. DAI intercepts, logs, and discards ARP packets with invalid IP-to-MAC address bindings. This capability protects the network from some man-in-the-middle attacks.
DAI ensures that only valid ARP requests and responses are relayed. The switch performs these activities:
.Intercepts all ARP requests and responses on untrusted ports
.Verifies that each of these intercepted packets has a valid IP-to-MAC address binding before updating the local ARP cache or before forwarding the packet to the appropriate destination
.Drops invalid ARP packets.
DAI determines the validity of an ARP packet based on valid IP-to-MAC address bindings stored in a trusted database, the DHCP snooping binding database. This database is built by DHCP snooping if DHCP snooping is enabled on the VLANs and on the switch. If the ARP packet is received on a trusted interface, the switch forwards the packet without any checks. On untrusted interfaces, the switch forwards the packet only if it is valid.
.PNG) IP Source Guard (IPSG)
IP Source Guard (IPSG)
IP source guard provides source IP address filtering on a Layer 2 port to prevent a malicious host from impersonating a legitimate host by assuming the legitimate host's IP address. The feature uses dynamic DHCP snooping and static IP source binding to match IP addresses to hosts on untrusted Layer 2 access ports.
Initially, all IP traffic on the protected port is blocked except for DHCP packets. After a client receives an IP address from the DHCP server, or after static IP source binding is configured by the administrator, all traffic with that IP source address is permitted from that client.
Traffic from other hosts is denied. This filtering limits a host's ability to attack the network by claiming a neighbor host's IP address.
.Verifies that each of these intercepted packets has a valid IP-to-MAC address binding before updating the local ARP cache or before forwarding the packet to the appropriate destination
.Drops invalid ARP packets.
DAI determines the validity of an ARP packet based on valid IP-to-MAC address bindings stored in a trusted database, the DHCP snooping binding database. This database is built by DHCP snooping if DHCP snooping is enabled on the VLANs and on the switch. If the ARP packet is received on a trusted interface, the switch forwards the packet without any checks. On untrusted interfaces, the switch forwards the packet only if it is valid.
.PNG) IP Source Guard (IPSG)
IP Source Guard (IPSG)IP source guard provides source IP address filtering on a Layer 2 port to prevent a malicious host from impersonating a legitimate host by assuming the legitimate host's IP address. The feature uses dynamic DHCP snooping and static IP source binding to match IP addresses to hosts on untrusted Layer 2 access ports.
Initially, all IP traffic on the protected port is blocked except for DHCP packets. After a client receives an IP address from the DHCP server, or after static IP source binding is configured by the administrator, all traffic with that IP source address is permitted from that client.
Traffic from other hosts is denied. This filtering limits a host's ability to attack the network by claiming a neighbor host's IP address.

IPv4/v6 Access Control List (ACL)
Packet filtering limits network traffic and restricts network use by certain users or devices. ACLs filter traffic as it passes through a switch and permits or denies packets crossing specified interfaces. An ACL is a sequential collection of permit and deny conditions that apply to packets. When a packet is received on an interface, the switch compares the fields in the packet against any applied ACLs to verify that the packet has the required permissions to be forwarded, based on the criteria specified in the access lists.
WoMaster supports L2-L7 ACLs, parsing up to 128 bytes/packet and L2-L7 packet classification and filtering IPv4/IPv6 traffic, including TCP, User Datagram Protocol (UDP), Internet Group Management Protocol (IGMP), and Internet Control Message Protocol (ICMP).
Multi-Level User Passwords
 Different centralized authentication servers are supported such as RADIUS and TACACS+. Using a central authentication server simplifies account administration, in particular when you have more than one switches in the network.
Different centralized authentication servers are supported such as RADIUS and TACACS+. Using a central authentication server simplifies account administration, in particular when you have more than one switches in the network.The authentication Chain is also supported. An authentication chain is an ordered list of authentication methods to handle more advanced authentication scenarios. For example, you can create an authentication chain which first contacts a RADIUS server, and then looks in a local database if the RADIUS server does not respond.
Network Management Software
NetMaster is the network management software for WoMaster devices. It can automatically discover network devices and put a topology diagram for the links. The batch configuration and upgrade helps system integrators install the system more easily.NetMaster provides ERPS group settings feature for batch Ring ID, Ring Version, control channel and Ring Ports configuration.
ERPS visualization is shown in NetMaster ERPS major ring and sub-ring info for the administrator.
VLAN information can also be shown in NetMaster with different colors on the port, device, and links. The trunk/access/hybrid ports are marked in blue/orange/grey color.


Full Support of G.8032 ERPS v2 Ethernet Ring Protection Switching
■ With G.8032 v.2 ERPS is tending to replace proprietary ring redundancy and standard Ethernet Ring Switching, as it provides stable protection of the entire Ethernet Ring from any loops. With the growth of the network scale, the calculation and response time in case of loop formation increases and could be from 2~120 sec to 5 minutes, and this is completely unacceptable in critical networks where the uninterrupted communication is required. Loops fatally affect network operation and service availability, thus, deploying network equipment with supported ITU-T G.8032 v2 ERPS with less than 50ms recovery time will significantly increase network reliability.
ERPS v2 also breaks the limitation of the proprietary ring that recovery time of Ring Coupling Link breakdown takes around 300 seconds. The proprietary ring and dual-homing topology cannot quickly respond to the foreign network changed (no topology changes) therefore delays the topology change. Adapting ERPS v2 Ring technology can quickly change topology, therefore, shorten the ring coupling link recovery time to 20ms.
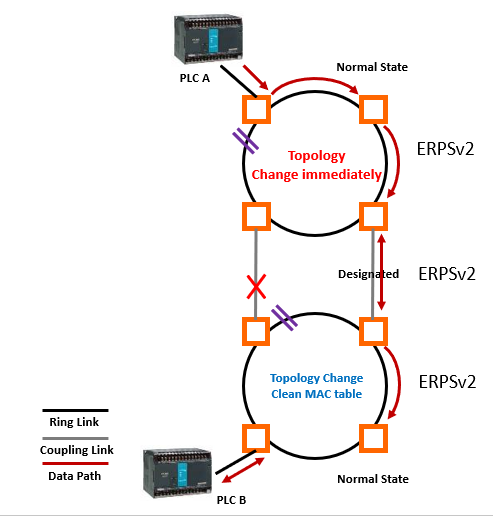

■ Enhanced Hardware CCM technology reduces Gigabit Copper Recovery time to 20ms

■ G.8032 ERPS v1 standard supported single ring topology, whilst G.8032 ERPS version 2 additionally provides recovery switching for Ethernet traffic in Multiple Ring of conjoined Ethernet Rings by one or more interconnections which saves deployment costs by providing wide-area multipoint connectivity with the reduced number of links.
