 Advanced Cyber Security
Advanced Cyber SecurityIndustrial Automation & Control System
 As the Industrial IoT (IIoT) demand continues growing , the closed industrial networks is facing challenges to be accessible over the public Internet. While it enhances operational efficiency, however, it brings more cyber security threats. The governments and enterprises are more concerned about the potential cyber security damages.
As the Industrial IoT (IIoT) demand continues growing , the closed industrial networks is facing challenges to be accessible over the public Internet. While it enhances operational efficiency, however, it brings more cyber security threats. The governments and enterprises are more concerned about the potential cyber security damages. The IEC 62443 Standard includes up-to-date security guidelines and a list of best practices for different parts of a network. It also includes information for those who perform different responsibilities on the network in order to protect against known security leaks and unknown attacks. The ultimate goal of the standard is to help improve the safety of networks and enhance industrial automation and control settings security.
At present, many system integrators, such as Siemens and ABB, require component suppliers to comply with the IEC 62443-4-2 subsection that specifically pertains to the security of end devices. This subsection defines four security threat levels.
.Level 1 is to protect against accidental and unauthenticated access.
.Level 2 is the baseline requirement of the automation industry. It relates to cyber threats posed by hackers, which is the most common attack experienced by system integrators.
.Levels 3 and 4 are against intentional access by hackers who utilize specific skills and tools.

From the viewpoint of cyber security experts, the major cyber security threats that can affect internal networks include unauthorized access, unsecured data transmission, unencrypted key data, incomplete event logs, and operational errors.

WoMaster provides SW & HW(ASIC) integrated protection mechanism, which applies the latest Application-Specific Integrated Circuit (ASIC) secure technology (L2-L7 packet classification), multi-level authentication, secure data transmission, encrypted key data, complete event logs/traps, operational errors prevention, and even logs, and operational errors exceeds IEC62443-4-2 Level 2 requirements to build most secure systems for industrial applications.
Advanced Port Based Security
IEEE802.1 x MAB (MAC Authentication Bypass)
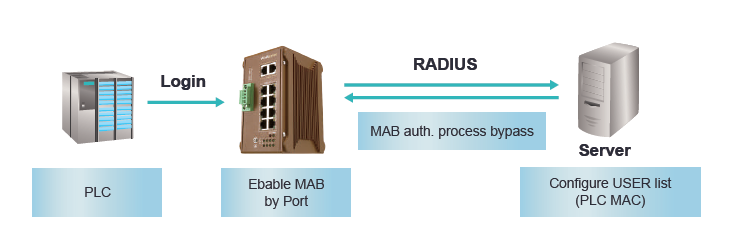
MAB enables port-based access control by bypassing the MAC address authentication process to TACACS+/Radius Server. Prior to MAB, the endpoint's (ex. PLC) identity is unknown and all traffic is blocked. The switch examines a single packet to learn and authenticate the source MAC address. After MAB succeeds, the endpoint's identity is known and all traffic from that endpoint is allowed. The switch performs source MAC address filtering to help ensure that only the MAB-authenticated endpoint is allowed to send traffic.
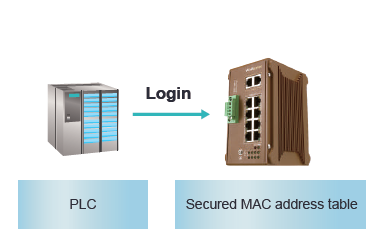 In addition to MAB, the authentication can also be done by the pre-configured static or auto-learn MAC address table in the switch.
In addition to MAB, the authentication can also be done by the pre-configured static or auto-learn MAC address table in the switch.
.MAC address Auto Learning enables the switch to be programmed to learn (and to authorize) a preconfigured number of the first source MAC addresses encountered on a secure port. This enables the capture of the appropriate secure addresses when first configuring MAC address-based authorization on a port. Those MAC addresses are automatically inserted into the Static MAC Address Table and remain there until explicitly removed by the user.
.The port security is further enhanced by Sticky MAC setting. If Sticky MAC address is activated, the MACs/Devices authorized on the port 'sticks’ to the port and the switch will not allow them to move to a different port.
.Port Shutdown Time allows users to specify for the time period to auto-shut down the port, if a security violation event occurs.

.The port security is further enhanced by Sticky MAC setting. If Sticky MAC address is activated, the MACs/Devices authorized on the port 'sticks’ to the port and the switch will not allow them to move to a different port.
.Port Shutdown Time allows users to specify for the time period to auto-shut down the port, if a security violation event occurs.

DHCP Snooping
DHCP snooping acts like a firewall between untrusted hosts and trusted DHCP servers. It performs the following activities:
.Validates DHCP messages received from untrusted sources and filters out invalid messages.
.Rate-limits DHCP traffic from trusted and untrusted sources.
.Builds and maintains the DHCP snooping binding database, which contains information about untrusted hosts with leased IP addresses.
.Utilizes the DHCP snooping binding database to validate subsequent requests from untrusted hosts. DHCP snooping is enabled on a per-VLAN basis. By default, the feature is inactive on all VLANs.You can enable the feature on a single VLAN or a range of VLANs.
Dynamic ARP Inspection (DAI)

DAI validates the ARP packets in a network. DAI intercepts, logs, and discards ARP packets with invalid IP-to-MAC address bindings. This capability protects the network from some man-in-the-middle attacks.
DAI ensures that only valid ARP requests and responses are relayed. The switch performs these activities:
.Intercepts all ARP requests and responses on untrusted ports
.Verifies that each of these intercepted packets has a valid IP-to-MAC address binding before updating the local ARP cache or before forwarding the packet to the appropriate destination
.Drops invalid ARP packets.
DAI determines the validity of an ARP packet based on valid IP-to-MAC address bindings stored in a trusted database, the DHCP snooping binding database. This database is built by DHCP snooping if DHCP snooping is enabled on the VLANs and on the switch. If the ARP packet is received on a trusted interface, the switch forwards the packet without any checks. On untrusted interfaces, the switch forwards the packet only if it is valid.
.PNG) IP Source Guard (IPSG)
IP Source Guard (IPSG)
IP source guard provides source IP address filtering on a Layer 2 port to prevent a malicious host from impersonating a legitimate host by assuming the legitimate host's IP address. The feature uses dynamic DHCP snooping and static IP source binding to match IP addresses to hosts on untrusted Layer 2 access ports.
Initially, all IP traffic on the protected port is blocked except for DHCP packets. After a client receives an IP address from the DHCP server, or after static IP source binding is configured by the administrator, all traffic with that IP source address is permitted from that client.
Traffic from other hosts is denied. This filtering limits a host's ability to attack the network by claiming a neighbor host's IP address.
.Verifies that each of these intercepted packets has a valid IP-to-MAC address binding before updating the local ARP cache or before forwarding the packet to the appropriate destination
.Drops invalid ARP packets.
DAI determines the validity of an ARP packet based on valid IP-to-MAC address bindings stored in a trusted database, the DHCP snooping binding database. This database is built by DHCP snooping if DHCP snooping is enabled on the VLANs and on the switch. If the ARP packet is received on a trusted interface, the switch forwards the packet without any checks. On untrusted interfaces, the switch forwards the packet only if it is valid.
.PNG) IP Source Guard (IPSG)
IP Source Guard (IPSG)IP source guard provides source IP address filtering on a Layer 2 port to prevent a malicious host from impersonating a legitimate host by assuming the legitimate host's IP address. The feature uses dynamic DHCP snooping and static IP source binding to match IP addresses to hosts on untrusted Layer 2 access ports.
Initially, all IP traffic on the protected port is blocked except for DHCP packets. After a client receives an IP address from the DHCP server, or after static IP source binding is configured by the administrator, all traffic with that IP source address is permitted from that client.
Traffic from other hosts is denied. This filtering limits a host's ability to attack the network by claiming a neighbor host's IP address.

IPv4/v6 Access Control List (ACL)
Packet filtering limits network traffic and restricts network use by certain users or devices. ACLs filter traffic as it passes through a switch and permits or denies packets crossing specified interfaces. An ACL is a sequential collection of permit and deny conditions that apply to packets. When a packet is received on an interface, the switch compares the fields in the packet against any applied ACLs to verify that the packet has the required permissions to be forwarded, based on the criteria specified in the access lists.
WoMaster supports L2-L7 ACLs, parsing up to 128 bytes/packet and L2-L7 packet classification and filtering IPv4/IPv6 traffic, including TCP, User Datagram Protocol (UDP), Internet Group Management Protocol (IGMP), and Internet Control Message Protocol (ICMP).
Multi-Level User Passwords
 Different centralized authentication server is supported such as RADIUS and TACACS+. Using a central authentication server simplifies account administration, in particular when you have more than one switches in the network.
Different centralized authentication server is supported such as RADIUS and TACACS+. Using a central authentication server simplifies account administration, in particular when you have more than one switches in the network.Authentication Chain is also supported. An authentication chain is an ordered list of authentication methods to handle more advanced authentication scenarios. For example, you can create an authentication chain which first contacts a RADIUS server, and then looks in a local database if the RADIUS server does not respond.

Network Management Software
NetMaster is the network management software for WoMaster devices. It can automatically discover network devices, and put a topology diagram for the links. The batch configuration and upgrade helps system integrators install the system more easily. NetMaster can also put alarm and reminder for cyber security.
 G.8032 v2 ERPS Resilient Network
G.8032 v2 ERPS Resilient NetworkWoMaster's managed Ethernet and Power over Ethernet switches provide the most resilient network by supporting the latest redundancy protocol ITU-T G.8032 v2 ERPS (Ethernet Ring Protection Switching), which is the first industry standard for Ethernet ring protection switching, achieved by integrating mature Ethernet operations, administration, and maintenance (OAM) functions and an automatic protection switching (APS) protocol for Ethernet ring networks.
Ethernet Ring Protection Switching (ERPS) protocol is defined by the International Telecommunication Union - Telecommunication Standardization Sector (ITU-T) to prevent loops at Layer 2. With the standard number is ITU-T G.8032, and ERPS is also called G.8032. Generally, redundant links are used on a network to provide link backup and enhance network reliability. The use of redundant links, however, may produce loops, causing broadcast storms and rendering the MAC address table unstable. These can affect the network, where the communication quality is not good enough, and communication services might be interrupted.
The Spanning Tree Protocol (STP), Rapid Spanning Tree Protocol (RSTP), and Multiple Spanning Tree Protocol (MSTP) are often used to prevent loops. STP meets network reliability requirements but provides slow convergence. Although RSTP and MSTP make enhancements, their convergence is still at the second level.
Compared with STP, RSTP and MSTP, ERPS has the following advantages:
◆ Fast network convergence
ERPS provides advantages of traditional ring network technologies such as STP/RSTP/MSTP and optimizes detection mechanism to provide faster convergence. For example, the ERPS-enabled switch provides 50-ms convergence for broadcast packets.
◆ Good compatibility
ERPS is a standard Layer 2 loop prevention protocol issued by the ITU-T. It can be used for communication between Womaster and non-Womaster devices on a ring network.
There were some basic concepts that support ERPS Ring.
・Ring Protection Link (RPL) – Link designated by mechanism that is blocked during Idle state to prevent loop on Bridged ring.
・RPL Owner node – Node connected to RPL that blocks traffic on RPL during Idle state and unblocks during Protection state.
・RPL Neighbor node – Node connected to RPL that blocks traffic on RPL during Idle state and unblocks during Protection state (v2).
・Link Monitoring – Links of ring are monitored using standard ETH CC OAM messages (CFM)
・Signal Fail (SF) – Signal Fail is declared when signal fail condition is detected.
・No Request (NR) – No Request is declared when there are no outstanding conditions (e.g., SF, etc.) on the node.
・Ring APS (R-APS) Messages – Protocol messages defined in Y.1731 and G.8032.
・Automatic Protection Switching (APS) Channel - Ring-wide VLAN used exclusively for transmission of OAM messages including R-APS messages.
G.8032 or ERPS use different timers to avoid race conditions and unnecessary switching operations.
・Delay Timers – RPL Owner used this to verify that the network has stabilized before blocking the RPL.
・Wait-to-Restore (WTR) timer – used to verify that SF is not intermittent.
・Wait-to-Block (WTB) timer – used to verify that no background condition exists (v2).
・WTB timer may be shorter than the WTR timer.
・Guard Timer – Used by all nodes when the state is change, it also blocks latent outdated messages from causing unnecessary state changes.
・Hold-off Timers – Used by underlying ETH layer to filter out intermittent link faults. Faults will only be reported to the ring protection mechanism if this timer expires.
For better understanding about ERPS, the understanding about what is loop is important. A loop is a configuration where a frame travels around a network without any ending it just going back to where it started. The figure below is an example of a simple loop.

We can say that a loop avoiding protocol has not been used on switches we could see where a frame could be sent from one switch to the next. It would keep going around and eating up bandwidth. Even more, the frames passing around the loop will cause trouble with the MAC address tables, where a network will not allow packets to pass through it.
After we understand about loops, we also understand that loops are not good things for our network but we would like to have the path redundancy that a loop provides. ERPS is one way of accomplishing this. An Ethernet ring consists of switches that form a closed physical loop. Each ring switch is connected to two adjacent Ethernet ring switches. This is the simple explanation about loop that we need to avoid earlier, but since the network using ERPS on it the network can work excellent.
ERPS Principles
Normal State

1. All nodes in a physical topology are connected to as rings.
2. ERPS blocks RPLs to prohibit formation of loops. In the figure above, the link between Node1 and Node4 is an RPL.
3. ERPS detects failures on each link between adjacent nodes.
Link Failure
 --->
--->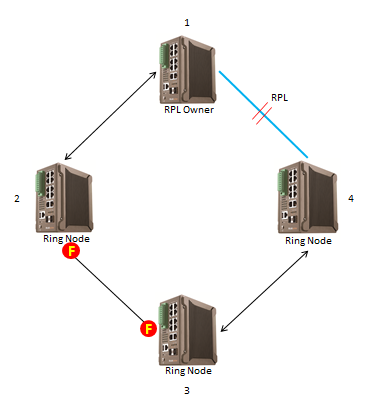
1. The nodes adjacent to a failed link block the failed link and send the R-APS(SF) message to notify other nodes in the ring of the link failure. In the figure above, the link between Node2 and Node3 fails.
2. After the hold-off timer expires, Node2 and Node3 block the failed link and send the R-APS(SF) message to other nodes in the ring.
3. The R-APS(SF) message triggers the RPL owner node to unblock the RPL port. All nodes update their MAC address entries and ARP/ND entries and the ring enters the protection state.
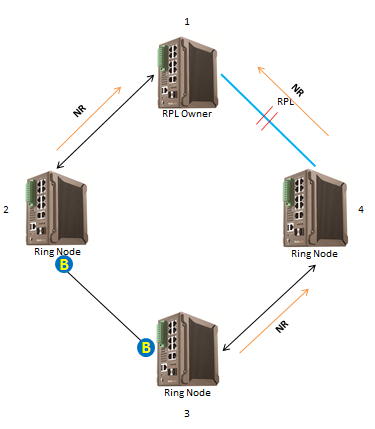
Failure Recovery
 --->
--->

1. When a failed link is restored, nodes adjacent to the link are still blocked and they send the R-APS(NR) message, indicating that no local failure exists.
2. After the guard timer expires and the RPL owner node receives the first R-APS(NR) message, the RPL owner node starts the WTR timer.
3. After the WTR timer expires, the RPL owner node blocks the RPL and sends the R-APS(NR, RB) message. And the ring state is pending, while waiting for the WTR timer expires.
4. After receiving the R-APS(NR, RB) message, other nodes update their MAC address entries and ARP/ND entries, and the nodes that send the R-APS(NR) message stop periodic transmission of the message and unblock the blocked ports. The ring network is restored to the normal state which is idle state.
Benefits of adapting G.8032 v2 Ethernet Ring Protection Switching
■ With G.8032 v.2 ERPS is tending to replace proprietary ring redundancy and standard Ethernet Ring Switching, as it provides stable protection of the entire Ethernet Ring from any loops. With the growth of the network scale, the calculation and response time in case of loop formation increases and could be from 2~120 sec to 5 minutes, and this is completely unacceptable in critical networks where the uninterrupted communication is required. Loops fatally affect network operation and service availability, thus, deploying network equipment with supported ITU-T G.8032 v2 ERPS with less than 50ms recovery time will significantly increase network reliability.


■ G.8032 v1 standard supported single ring topology, whilst G.8032 version 2 additionally provides recovery switching for Ethernet traffic in Multiple Ring of conjoined Ethernet Rings by one or more interconnections which saves deployment costs by providing wide-area multipoint connectivity with reduced number of links.

■ Important to note, deploying switches supporting G.8032 v2 ERPS provides economical and highly resilient Ethernet infrastructure, as they can interoperate with third party switches and still guarantee fast network recovery time without any data loss.
.png)
ERPS ring is one of technology that ideal for every application, this technology currently has provided the best option. If you still want to know more, please contact us athelp@womaster.eu


.jpg)